I will be posting a new blog series for co-management in the coming months. This post will highlight the undesirable effect some Group Policies will have on a successful co-management Intune enrollment.
Co-management will allow you to automatically enroll your SCCM clients into Intune, if they are in scope.

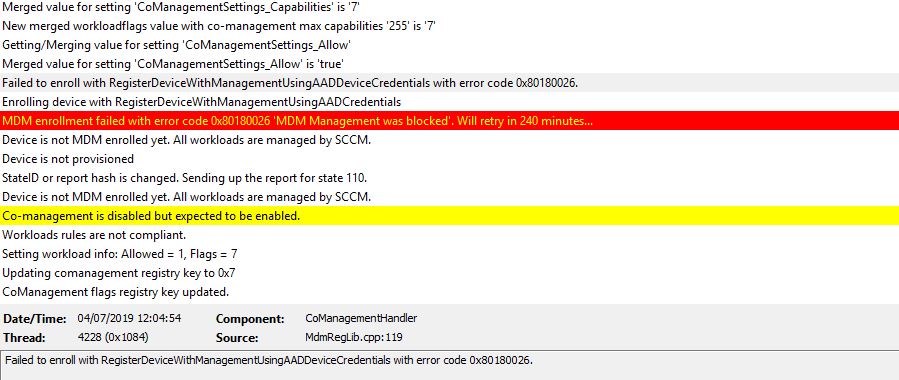
Recently I was asked to look at why some clients were failing enrollment. The customer was seeing the following error in CoManagementHandler.log
Failed to enroll with RegisterDeviceWithManagementUsingAADDeviceCredentials with error code 0x80180026
Error in CoManagementHandler.log
If we take a look at the Microsoft Docs:-
https://docs.microsoft.com/en-us/windows/win32/mdmreg/mdm-registration-constants
MENROLL_E_DEVICE_MANAGEMENT_BLOCKED
Source: https://docs.microsoft.com/en-us/windows/win32/mdmreg/mdm-registration-constants
0x80180026
Mobile Device Management (MDM) was blocked, possibly by Group Policy or the SetManagedExternally function
Sure enough, when we checked Group Policy, the customer had the following GPO targeted to the Co-Management Pilot group
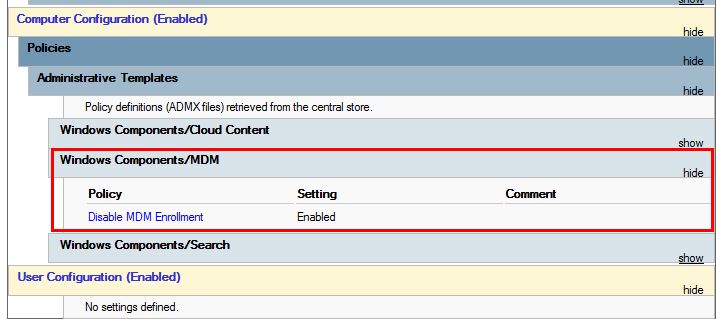
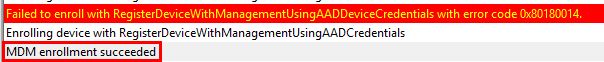
As soon as we took the Co-Management Pilot group out of scope for the above Group Policy Item, MDM enrollment was successful
Conclusion
Always check you don’t have any conflicting GPO’s when configuring Co-management. The GPO will overrule the Configuration Item that is received by your SCCM client when it is configured for co-management
Whats coming…
There is an improved registration process using the Azure AD Device token in SCCM Technical Preview 1906 for MDM enrollment.
To support this new enrollment behavior, clients need to be running Windows 10 version 1803 or later
https://docs.microsoft.com/en-us/sccm/core/get-started/2019/technical-preview-1906#bkmk_comgmt
